Here I mainly focus those who use Azure AD as their single sign on multi tenant applications and application session is time out within 10 minutes.
we are going to change Azure AD default Access Token Lifetime settings to increase session time out.
when you try to figure out what was the root cause of this session time out and you don't know where this parameter cause. but you can see on chrome developer mode there is a token which expires in blahblahblah.00 seconds
If you are using Azure AD to authenticate your application user you should definitely use Access Token Lifetime to manage your application sessions
A token lifetime policy is a type of policy object that contains token lifetime rules. Use the properties of the policy to control specified token lifetimes. If no policy is set, the system enforces the default lifetime value.
I will explain how to set a policy and make it default with increase the session timeout to six (6) hours
we are going to change Azure AD default Access Token Lifetime settings to increase session time out.
when you try to figure out what was the root cause of this session time out and you don't know where this parameter cause. but you can see on chrome developer mode there is a token which expires in blahblahblah.00 seconds
 |
| don't misunderstand about this image. i have taken this after fix |
If you are using Azure AD to authenticate your application user you should definitely use Access Token Lifetime to manage your application sessions
A token lifetime policy is a type of policy object that contains token lifetime rules. Use the properties of the policy to control specified token lifetimes. If no policy is set, the system enforces the default lifetime value.
 |
| Token Lifetime Properties |
I will explain how to set a policy and make it default with increase the session timeout to six (6) hours
- Download the latest Azure AD PowerShell Module Public Preview release.
- Open Power-Shell as Administrator
- Run following command in power-shell
- Click “A” to install all
- Connect new tenant Azure AD to set Access Token Lifetime
- Run following command to connect to Azure AD
- Enter tenant administrator user name and password
- Run the following command to add Access token key policy to 6 hours
- To see your new policy, and to get the policy ObjectId, run the following command
- Assign the policy to your service principal
- Assign the policy to your service principal. You also need to get the ObjectId of your service principal.
- For each tenant you must find service principle ID from Azure RM Accounts
- Open new PowerShell windows as an Administrator
- Run following command:
- Use new tenant administrator credentials to log in
- Run following command: Get-AzureRmADServicePrincipal
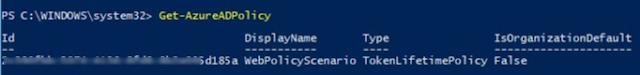
- Find out the correct App registration name and find the ID of that App
- Enter below command to assign the policy
- Add-AzureADServicePrincipalPolicy -Id < Service Principle App Registration ID> -RefObjectId < ObjectId of the Policy >
4. Set the policy default true
- Run following command to set policy as default
- Set-AzureADPolicy -Id < policy id > -IsOrganizationDefault $true










No comments:
Post a Comment